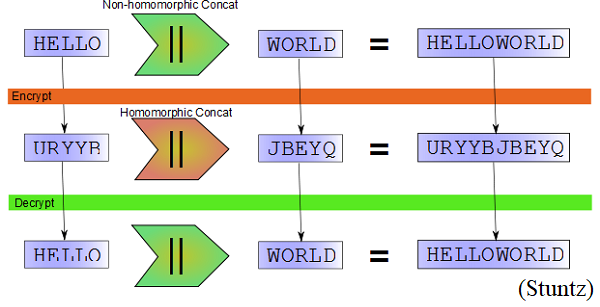
Traditional standard encryption methods provide security to data in storage state and transmission state. But in processing state, performing operations on data require decryption of data. At this state data is available to cloud provider. Hence traditional encryption methods are not sufficient to secure data completely. (Chauhan et al.)
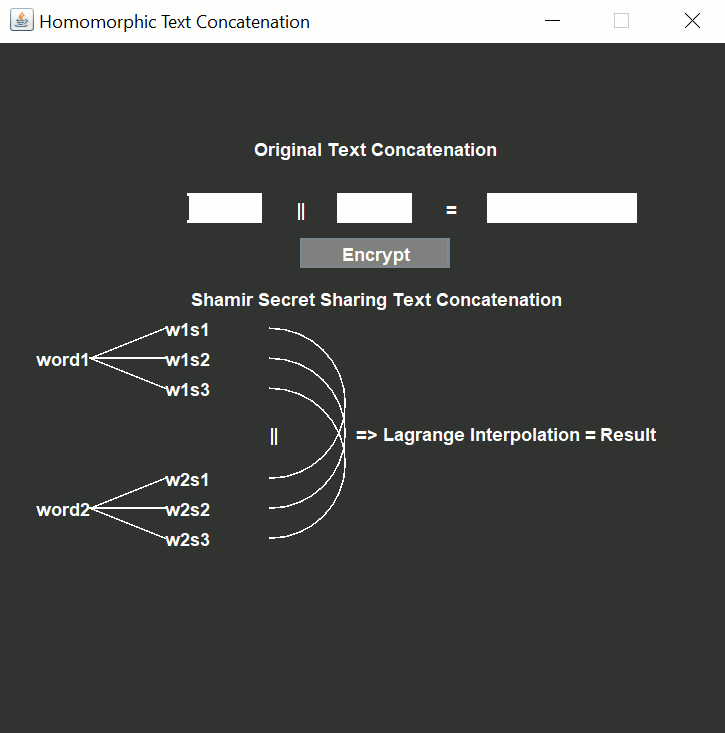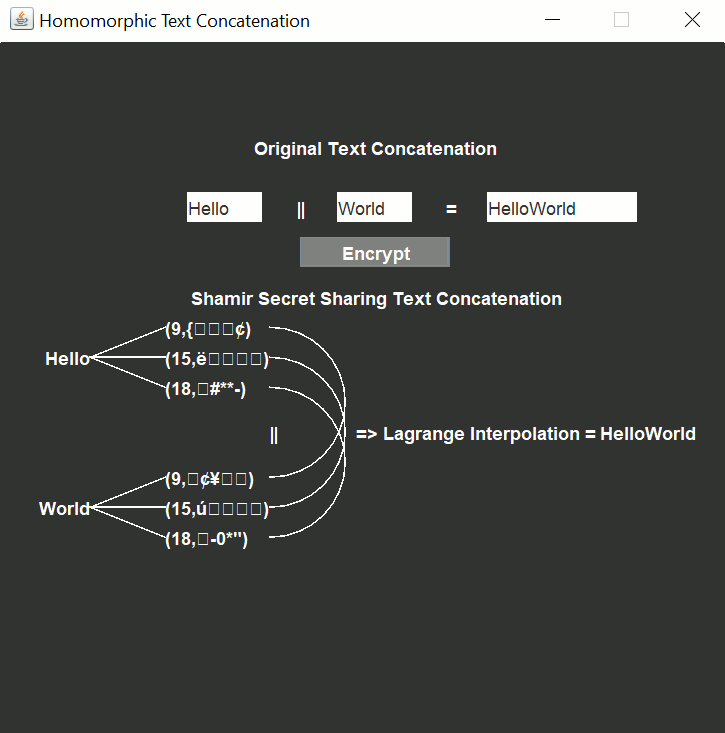
Click one of the following links to download a demo of homomorphic text encryption using Shamir's Secret Sharing: